After Conducting Reconnaissance What Should You Know About the Network or Organization
Agile vs Passive Cyber Reconnaissance in Data Security

Cyber Reconnaissance is the kickoff pace of whatever professional penetration exam. In this phase the goal is to get together as much information well-nigh the target as possible. This includes technical information about it'south network topology and systems. But information technology also includes information on employees and the company itself that may be useful in the later on stages of the penetration test. The more information you get together during the reconnaissance phase the more likely yous are to succeed in the later stages of the penetration exam. There are two types of cyber reconnaissance that you tin perform active information gathering and passive data gathering.
Passive Cyber Reconnaissance
Passive recon is when yous gather data nigh a target without directly interacting with the target. This means that yous don't ship any type of request to the target and therefore the target has no mode of knowing that you are gathering data on them. Generally passive data gathering uses public resources that have data on that target. Using public resources to get together information is called Open source intelligence (OSINT). Using OSINT you tin gather things such as IP addresses, domain names, e-mail addresses, names, hostnames, dns records and fifty-fifty what software is running on a website and it'south associated CVE's. Here are some common tools penetration testers use for passive information gathering:
Google Hacking (search engines): You can use custom search queries in google, bing and other search engines to detect data such as usernames, passwords, hidden web pages, hidden files, metadata and more. People oft use a resource called the google hacking database, which is a gratuitous online tool that stores useful google search queries that have been known to return interesting results.

Netcraft: Netcraft is used to find information related to a domains network, SSL/TLS, hosting history, owner, associated addresses and email, parent organization, domain registrar and more.
Shodan: This is a very popular tool used to identify IOT devices and network devices over the net. Information technology gives information such as potential vulnerabilities, Internet service provider, hostnames, country, open ports, SSL document information, encryption algorithms and more.
Active Cyber Reconnaissance
Active recon is when you interact directly with a computer arrangement in club to gather system specific information about the target. Unlike passive information gathering that relies on publicly available information, active information gathering relies on tools that will transport dissimilar types of requests to the computer. The goal is to gather information almost that device or other devices that are continued to information technology on the same network. Active recon can exist used to find out information such as open/closed ports, the Os of a machine, the services that are running, banner grabbing, discovering new hosts or notice vulnerable applications on a host. The chief drawback of agile reconnaissance compared to passive reconnaissance is that direct interaction with the host has a chance of triggering the systems IDS/IPS and alerting people to your activity. Here are some of the nearly normally used active information gathering tools:
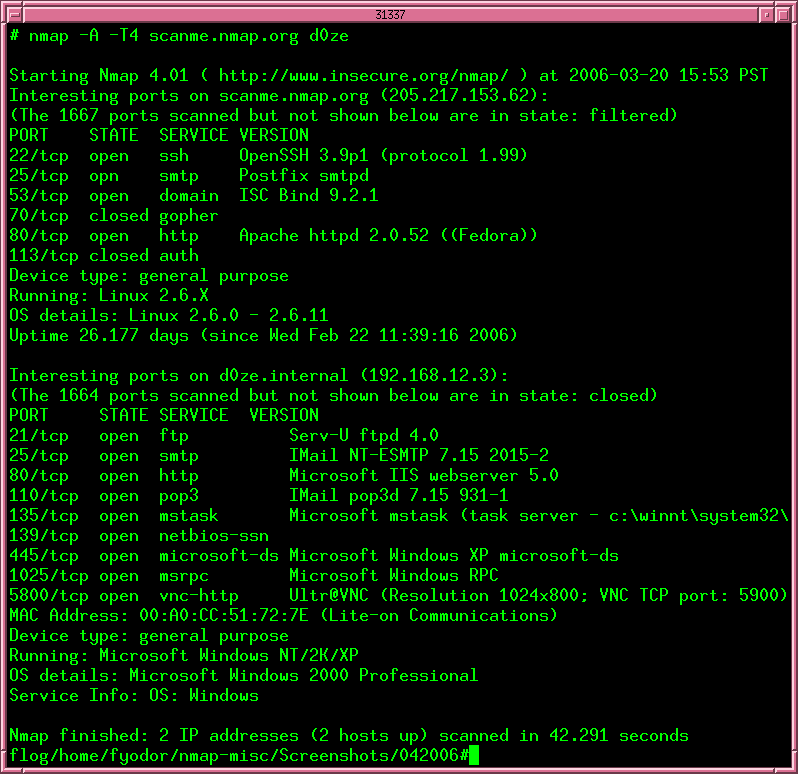
Nmap: Nmap is an open source network mapper and port scanner. This means information technology can be used to perform ping sweeps that discover new hosts besides every bit scan currently known hosts to find data on; what ports are open, what services are running on those ports, the machines operating systems and with some configuration known CVEs associated with those services.
Nessus: Nessus is a commercial vulnerability scanner. Information technology scans hosts and identifies vulnerable applications running on that host in an organized written report. Unlike nmap this tool is non free, but it provides very comprehensive reports and is widely used within the industry.
Nikito: Nikito is a free command line spider web server scanner that identifies vulnerabilities on web servers. This includes dangerous files, outdated server software and other common problems.
Active vs Passive cyber reconnaissance what is the difference?
The main difference between active and passive cyber reconnaissance are the methods they use to gather information. Active recon tools interact direct with the systems in order to gather organisation level data while passive recon tools rely on publicly available information. Equally a outcome, active recon tools tend to gather more than useful information but run the take a chance of alerting the owner of the car of your activities.
Typically penetration testers use both methods to collect data on their target. Both types of cyber reconnaissance can uncover data that will bear witness vital in the class of the penetration test.
Conclusion
Cyber reconnaissance is a critical role of the penetration testing procedure. The information that you find in this pace volition dictate what you practise in the other steps of the test. When doing reconnaissance you can practise passive data gathering, using public resources to obtain data virtually the company, it's employees or the engineering science that they use. You can also use active information gathering techniques to gather system level information most specific systems the target owns, such equally the Os, the services that machines runs and open/closed ports. Both types of data gathering are important and a good penetration tester will utilize both to find the best method for breaching the visitor.

Popular
More Topics
Sign upwards to read more than!
Source: https://www.securitymadesimple.org/cybersecurity-blog/active-vs-passive-cyber-reconnaissance-in-information-security
0 Response to "After Conducting Reconnaissance What Should You Know About the Network or Organization"
Post a Comment